It's Easy To Stay Safe Online
Keep Your Data Private
Data privacy might seem like an abstract concept, but it couldn't be more personal. Your data is worth a lot of money to many different people, businesses and organizations. but we often don't value our own data story as much as they do. To become a "data snob" and value your data as much as big tech companies do, remember the Silicon Valley adage: if you're not paying for it, you're the product. The global data analytics market was estimated to be worth over $270 billion in 2022 and is projected to reach $650 billion by the end of the decade. You and your data makeup a slice of this multibillion-dollar bonanza
Tips!
- Know what you can't control - It is impossible to control who has access to all of your data. Understand that there is a tradeoff between convenience and privacy. However, it is important to understand that convenience and privacy come at a cost; you may need to share more data in order to fully utilize the features of devices, apps, and software. Therefore, be aware of this balance in order to make better decisions concerning your data. By understanding this balance, you can make more informed data decisions.
- Cultivate a data privacy habit - Develop a habit of being mindful of data privacy. Fortunately, many web browsers, computers, and devices will ask you if you want to share certain types of data with a new app or website. When signing up for websites, apps, or software, be aware of the type of data requested and think about what you are willing to share. Commonly asked for data includes location, contacts, photos, camera access, and usage behavior. Whenever possible, opt for limiting access to data only when using the app. If an app is not functioning without sharing more data than necessary, search for an alternative. It is recommended to err on the side of caution and limit how much data is shared.
- Check your settings - Check your device's settings regularly to ensure that all app and software permissions are set according to your comfort level. Default settings to usually turn off include camera, microphone, location, and contact syncing. You can access app and software permissions through your device's general settings. Disallow access to permissions unless they are necessary for the app to function properly and you trust the app. Remember, apps will often ask for you to give them always access to permissions, but you usually only need to give them permissions for while you are using the app.
- Camera - off
- Microphone - off
- Location - off
- Sync contacts - off
- Delete apps you don't use - Periodically conduct an "app audit" to evaluate the apps installed on your devices. Consider whether you have used each app recently or if it is collecting and sharing data without you knowing. Many apps will collect and share your device-use data even when you don't use them; you're basically giving away your data. If it has not been used for a few months, delete it to ensure that it does not access any of your data. Remember, you can always reinstall the app if needed.
What is a Phishing Scam ?
Phishing is a form of internet scam where a person with malicious intent pretends to be someone else to obtain data that they shouldn’t have access to. This can be done through email, phone calls, text message or social medias. No one is immune to falling for a phishing attacks. By knowing how to recognize, recover, and report phishing you can protect yourself and others from phishing attempts.
Recognize
- Telltale Signs of a Phishing Attack:
- Is sender Email address legit? Even if the address looks right, is it strange or unexpected?
- Is the message urgent, unexpected or too good to be true?
- Is it asking you to click a link or file? (hover over to check first)
- Is it asking you to login to a site looks familiar or download a file? (check URL even if the site looks right)
- Does it look unprofessional, with misspellings and improper grammar?
- More info at to recognize phishing scams.
Recover
- If you login to an unknown site, change your passwords immediately
- Scan your device with an anti-virus software and turn on automatic updates
- Make sure Multi-factor Authentication ( MFA) is turned on for additional security
- Backup your data
- If your information is lost or exposed, follow the steps at .
Report
- Alert other people not to click or respond to the phishing email
- Use the "Forward" button to send it when reporting to Phish@kent.edu
- If you got a phishing , forward it to SPAM (7726)
- Report fraud to
Why Should You Update Your Devices?
Software update reminders can be annoying and interrupt your workflow. Given that no software release is ever perfect, new exploits are identified regularly, and malicious actors look for systems with vulnerabilities, timely response is important and will help keep you safe. Although the process of updating your software can get tedious, but the sooner you update, the sooner you'll secure yourself.
Best Software Update Practices:
- Turn on automatic updates wherever possible.
- Only get updates from official software sites and built-in update utilities, and not from email links or web browser pop-ups.
- Be mindful of personal devices. Devices like security cameras, smart home accessories, and digital assistants all provide convenience, but require updates to maintain safety and privacy.
- Don’t just worry about updating your device, make sure the apps on your devices are also regularly updated as well
Examples of Malicious update notifications:
Notice how they are browser pop-up ads and are using but not exact company logos. Stay clear of clicking any of these pop-ups and close them as soon as you can.

Example 1: Notice the .biz link, have you ever seen that before? There are also grammatical errors throughout the page, "often the cyber criminals to block". Does that seem very official? Always go through official websites to update software.
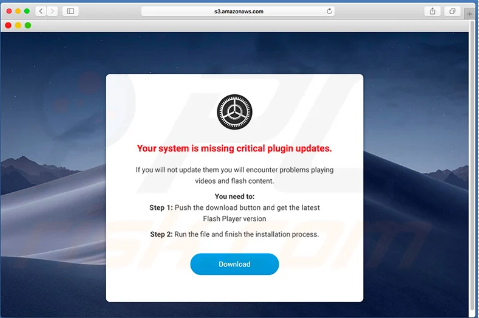
Example 2: The urgency of this message is a red flag that it is not legitimate. Once again notice the link, do you think Adobe Flash would send you off of their site for a download?

Example 3: The count down is a clear indicator that this is a fake download. You will never receive a message from Apple through your browser. Avoid installing anything that is not from the official app store.
For questions, please email security@kent.edu or visit /it/secureit
#BeCyberSmart #CyberSecurity
Protecting Yours and University Data
One of the biggest threats in cybersecurity is the loss of data. Not knowing the intention of the individual that steals information can become a nightmare. Protecting online data is simple and can be easily done. Here are some examples of steps you can take to protect your data.
- Do not save your credit card or personal information in your browser.
- Think before you text/email any Personal Identifiable Information or (PII).
- Does the other party need the information?
- Could this information be misused if someone with malicious intent got ahold of it?
- Avoid using the same password for multiple accounts to reduce risks.
- Avoid clicking on popups or links even if they look legitimate. They could be fake:
- Check if the link has a secure internet browser address (
https) on the pop up and your browser should not display any virus alerts.
- Check if the link has a secure internet browser address (
This week we will also be doing a scavenger hunt. In this we will have you search SecureIT website and find some useful information to help protect your data online.
Data Classification:
Not all data is created equal. Some are more sensitive than others and need to be kept confidential no matter if it is yours or others. Some data are restricted by law due to privacy and security reasons. Have you heard of FERPA, HIPAA, COPPA and GDRP? These are all laws to regulate organizations to protect privacy. Here are the details on . KSU Employees: Please explore our to learn more about Data Classification Standards and Data Governance.
Backing Up Your Data:
It is a good practice to regularly back up important data and to delete or offload anything that is not necessary. There is the 3-2-1 rule for backing up data.
3 Copies of your data should be kept.
2 Different types of storage.
1 Copy kept somewhere off site, like the cloud.
Safe Email Practices:
Ever since the first email was sent back in 1971 it has been one of the most used methods for communicating and distributing information for many purposes. Here are some good rules to follow when sending an email.
- Avoid sending any sensitive information in your email.
- This includes information such as your credit card information, PII, and FERPA.
- If you absolutely must send out sensitive information:
- Make sure the person receiving information really needs it, verify person and their email.
- Encrypt sensitive information to make sure the content is secure and safe.
- Instructions for encrypting
- Instructions for encrypting
- Don’t ask for sensitive info in a mass email.
- If sensitive information is requested in massive chain email, please inform the sender if it is a mistake and don’t reply to ALL.
For questions, please email security@kent.edu or visit /it/secureit
#BeCyberSmart #CyberSecurity
Protect Your Accounts
As more and more of our lives move into the digital space, it is important to keep all of our accounts secure. Every time you sign up for a software, social media, or any website that requires your personal information, you are putting your information at an elevated risk. As a result it is important that you are aware of what information you are sharing on the internet, ensure that you take the steps to protect your accounts properly. Keep reading for a chance at winning a prize in this week's activity!
PASSWORD PRACTICES, DO'S AND DON'TS
Because a creating a password is the first and most basic step taken to secure your account, having a strong one is important. Here are some basic guidelines for creating a secure one.
- Do:
- Create a Unique Password
- Use Passphrases
- Use a Password Manager
- Include a Special Characters & number in Your Password
- Make Your Passwords Long (16 characters or more)
- Don't:
- Reuse Your Passwords/Passphrases
- Store Passwords In Your Browser
- Use Personally Identifiable Info (e.g. Your Name)
- Use a Common Password (e.g. password123)
- Use Dictionary words
What is MFA?
Multifactor Authentication (MFA) is one of the best ways to boost your accounts security. Here are some benefits:
- Reduces risk of compromised passwords
- Increases security with something you know
- Complies with single-sign-on
- It adds next level security even remotely
- It's easy to use
Why You Should Be Using A Password Manager
In average, most people have over 100 accounts. How can one remember 100 unique and complex passwords? This is where a password managers role lies. A password manager is software created to manage all your online credentials like usernames and passwords. It stores them in a safe, encrypted database and also generates new passwords when needed. Use a password manager to help manage different passwords across your accounts and services. The best ones work for all browsers and devices. You can learn more by , Here are some benefits of using one:
- Saves time
- Works across all your devices and operating systems
- Protects your identity
- Notifies you of potential phishing websites
- A better way to share passwords with people you trust
- Notifies you when you use weak or compromised passwords

